What Is A Drive By Download
My last blog post focused on Java exploits and the need to keep all software up to date. Since writing that article I have received some questions from customers asking for more details on how attackers are using such vulnerabilities to compromise systems. Subsequently, this two-part blog post is dedicated to the topic of drive-by download attacks – a popular tactic among attackers for taking advantage of software that has not been kept up to date. For these articles, I’m drawing on the data and analysis we published in various volumes of the Microsoft Security Intelligence Report. There are several variations of drive-by download attacks: exploits are often distributed through Web pages, as well as e-mail and instant messaging (IM) services. I will focus on one variation, Web pages, to keep these articles shorter than it would be otherwise.
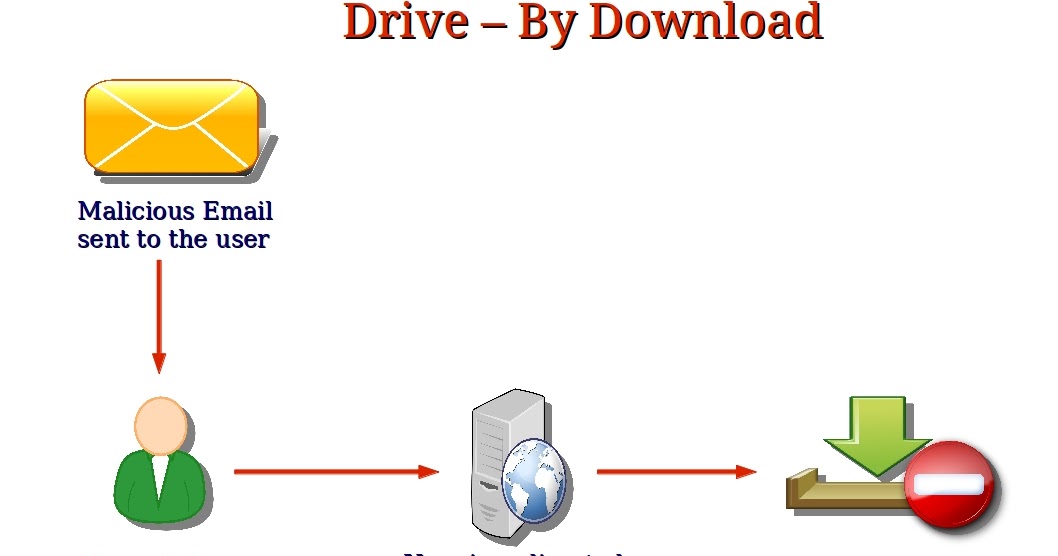
In this video our Cisco Umbrella research team explains the cyber threat, drive-by download. A drive-by download site is a website that hosts one or more exploits that target specific vulnerabilities in web browsers, and browser add-ons. Malware distributors use various techniques to attempt to direct Internet users to Web sites that have been compromised or are intentionally hosting hostile code.
A drive-by download site is a website that hosts one or more exploits that target specific vulnerabilities in web browsers, and browser add-ons. Malware distributors use various techniques to attempt to direct Internet users to Web sites that have been compromised or are intentionally hosting hostile code. Users with vulnerable computers can be secretly infected with malware simply by visiting such a website, even without attempting to download anything themselves.
How to Download to a Flash Drive by Steve McDonnell. Flash drives are chips of memory you can use to store music, pictures and other data. The memory retains what you copy to it even when there's no power connected. Flash drives are a faster alternative to mechanical disk drives, however they typically come in smaller sizes because they are. A drive-by download is a download of a program that initiates without a user's consent, or under circumstances where a user does not understand what is being consented to. Such downloads are used to install adware, spyware, and other malware on user computers and they are very common in some corners of the Internet.
This technique usually involves posting exploit code to a legitimate website, either by gaining access to the site through intrusion or by posting malicious code to a poorly secured Web form, like a comment field on a blog. In most cases, the exploit code itself is hosted on a different website and is exposed through the compromised webpage using a technique like a URL embedded in malicious script code or an inline frame, called an IFrame for short. An IFrame is an HTML document that is embedded in another HTML document.
During a drive-by download attack, an IFrame is typically used to load a separate HTML page into a window on the current page. Inline frames can be as small as a single pixel making them impossible to detect with the naked eye. Because the IFrame loads another webpage, it can be used by criminals to place malicious HTML content, such as a script that downloads and installs malware, into non-malicious HTML pages hosted by trusted websites.
Attackers typically target vulnerabilities in Web browsers or in browser add-ons, such as ActiveX controls, that enable users to experience popular types of media content within the browser environment. In some cases, these add-ons are preinstalled by the computer manufacturer before the computer is sold. The user may not even use the vulnerable add-on or be aware that it is installed. Much of this software has no facility for updating itself, so even when the software vendor publishes an update that fixes the vulnerability, the user may not know that the update is available or how to obtain it, and remains vulnerable to attack.
- The term drive-by download describes how malware can infect your computer simply by visiting a website that is running malicious code (Stage 1: entry point). Most of the time, these are legitimate websites that have been compromised to redirect you to another site controlled by the hackers (Stage 2: distribution).
- A drive-by download refers to the unintentional download of malicious code onto a computer or mobile device that exposes users to different types of threats.
Most malicious Web sites use “exploit kits” that package together several exploits. Exploit kit creators continually update their kits, removing poorly performing exploits and replacing them with new ones. The exploits included in an exploit kit typically target vulnerabilities affecting several different platforms, browsers, and add-ons from different software vendors in an effort to ensnare as many potential victims as possible. Clearly different attackers have different philosophies on the number of exploits to include in the exploit kits they use. For example we have found some exploit kits with as many as 23 exploits packaged together. I call this the “lottery strategy” as these attackers seem to be leveraging so many different exploits in one kit in an attempt to maximize the chances that they find one unpatched vulnerability on systems that end up encountering it. Other attackers choose to package only two or three reliable exploits for prevalent vulnerabilities in their exploit kits. Presumably these attackers are getting an acceptable return on their investment and don’t see the necessity of including more exploits in their kits.
The Microsoft Security Intelligence Report volume 8 contains data on the specific browser based vulnerabilities we observed being actively targeted during the second half of 2009. This data will give you an idea of the types of software attackers are targeting in drive-by download attacks.
Please feel free to contact us for any questions. Features: * Free to download * Includes more than 100 animal sounds * Press the menu icon for the options * Mark as favorite * Set as ringtone, notification, alarm and assign to contacts * Easy to use UI Enjoy these free Animal Sounds ringtones! This app offers many and varied animal sounds of exceptional quality. Animal ringtones for free. This is the perfect app to have a good time with your children or simply to laugh a little with your friends!
Figure: top 10 browser-based exploits, by percentage of all exploits each month, in the second half of 2009
Web pages that host drive-by download attacks, and malware hosting sites, are found all over the world in different concentrations. The number of drive-by hosting sites in any given location is highly dynamic and can change rapidly. The data below was published in the Microsoft Security Intelligence Report volume 11. One thing to keep in mind about this data is that systems hosting drive-by downloads and malware hosting sites are typically compromised systems and their owners do not know they are being used to attack other Internet users.
What Is A Drive By Download Attack
Figure on the left: Drive-by download pages in the second quarter of 2011 by percentage of all URLs in each country/region; figure on the right: Malware distribution sites per 1,000 Internet hosts for locations around the world in the second quarter of 2011
What Is A Drive By Download Attack
Figure on the left: Highest percentages of all URLs of drive-by download pages by location in the first quarter of 2011 (1Q11) and the second quarter of 2011 (2Q11) compared to the worldwide average; figure on the right: Malware distribution sites per 1,000 Internet hosts for locations around the world in the first quarter of 2011 (1Q11) and the second quarter of 2011 (2Q11) compared to the worldwide average
In my next blog post in this two-part series I will provide some guidance on how systems can be protected from drive-by download attacks.
Sql Injection
Tim Rains
Director
Trustworthy Computing